How to Setup AWS VPC For Fargate Deployment
-
 Chinthaka Dinadasa
Chinthaka Dinadasa - 05 Jul, 2023

When deploying your containers on Fargate, it is crucial to set up a Virtual Private Cloud (VPC) properly to ensure security, networking, and connectivity.
In this article, we will provide a comprehensive guide on setting up an AWS VPC for Fargate deployment.
If you are familiar with Terraform you can quickly check our guide on How to Build AWS VPC Using Terraform – Step By Step and build the same VPC requirement through Terraform.
VPC Requirement
Here for this article series, we are going to set up VPC with the following components.
-
4 Subnets (2 subnets from each public and private subnet in 2 availability zones)
-
Internet gateway for granting internet access from the public subnet.
-
NAT Gateway for granting internet access from the private subnet (One way)
-
Route table entries to bring subnet traffic through the bound network connection (Internet gateway or NAT gateway.)
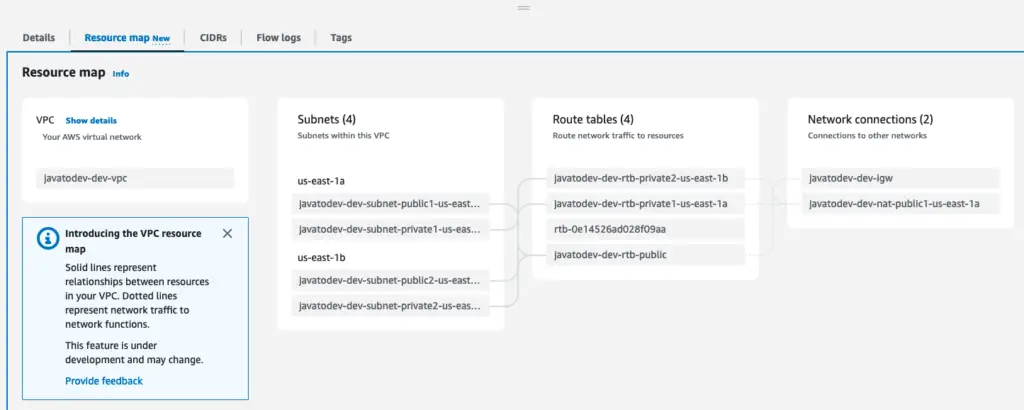
VPC Resource Map for the VPC created for fargate deployment.
VPC Setup Creation Steps
Now creating VPC is really easy with the AWS dashboard. Use Create VPC option under VPC product dashboard and add your preferred VPC name.
Then AWS will automatically configure whole subnets, and route tables with network connection under preferred availability zones.
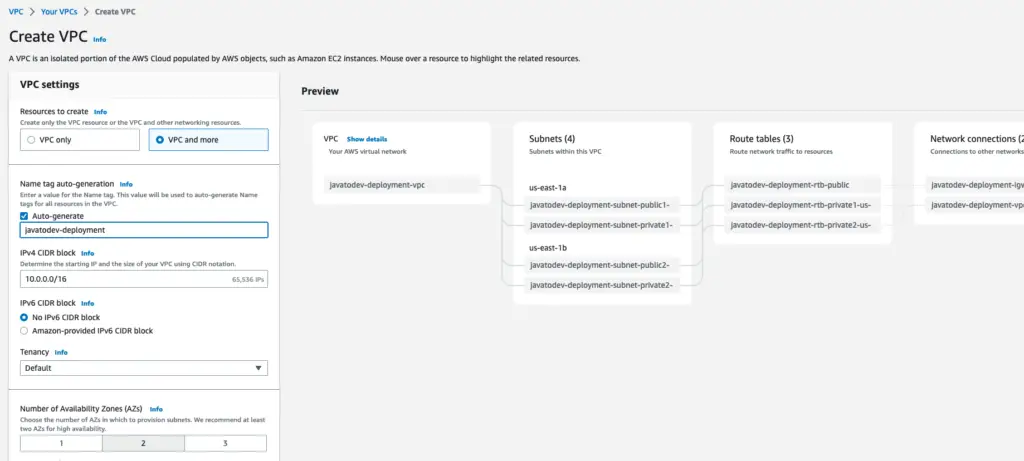
Create VPC through AWS dashboard
Here we should have an internet gateway and a NAT gateway**.**
by default, AWS suggest keeping 2 NAT gateways in both availability zone to keep internet access to the private subnet in availability zone unavailability.
But for demonstration purposes, we can go with a single NAT gateway on a selected availability zone.
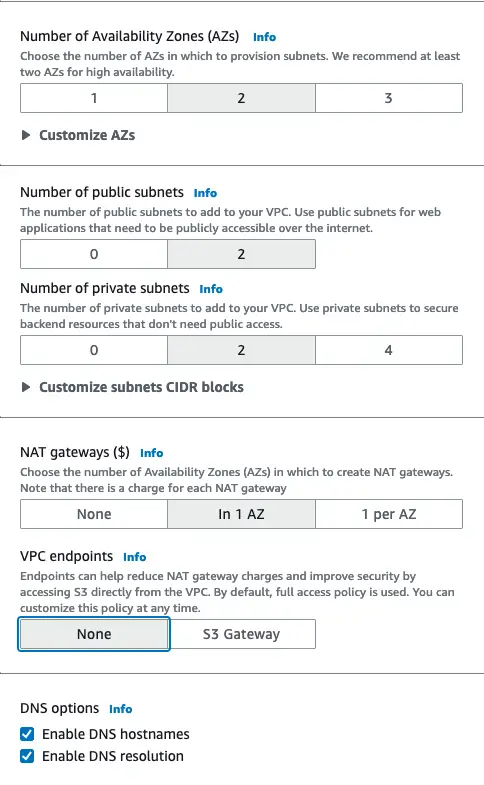
Subnet configurations on VPC creation
CIDR Blocks Setup
For this VPC, we are going to use 10.0.0.0/16 which includes 65,536 available IPs for IPv4 CIDR block.
Additionally, we can have the following CIDR blocks for subnets CIDR blocks.
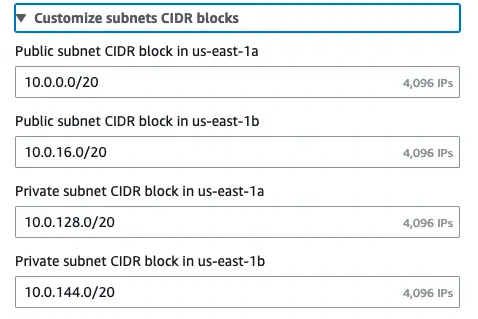
Customize subnet CIDR blocks for each subnet in AZ
All done, now we can proceed with VPC creation, and this might take few minutes since we have NAT gateway attached to the VPC private subnets.
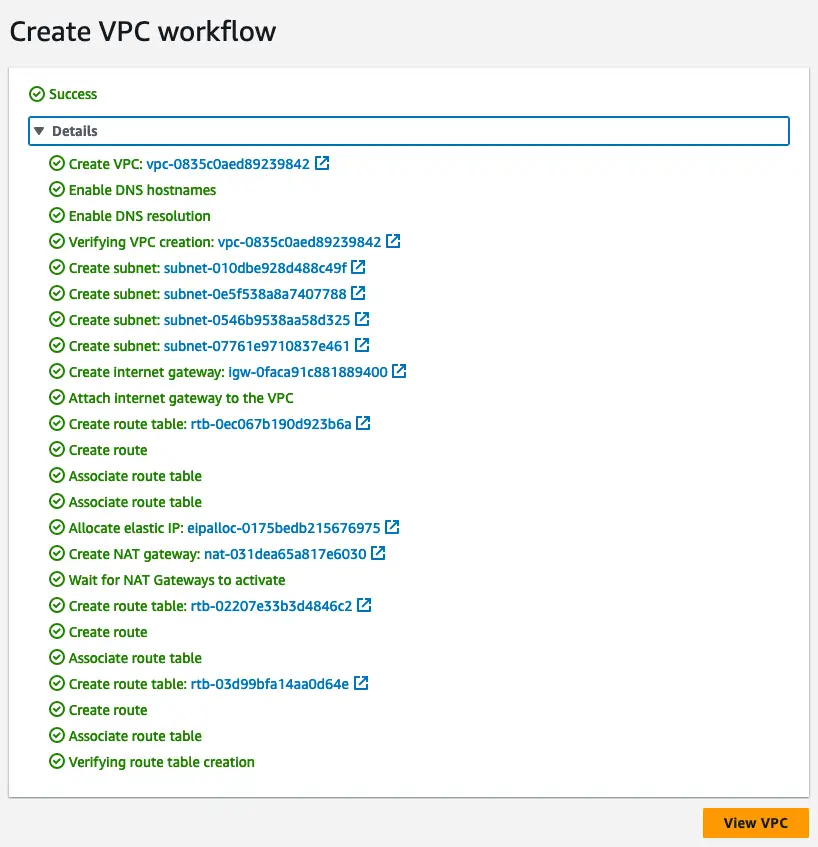
Create VPC status view in the AWS dashboard
Conclusion
We’ve completed setting up AWS VPC for spring boot application deployment with ECS fargate.
After this VPC setup, we can proceed with Amazon ECR (Amazon Elastic Container Registry) creation and publishing application docker images to the ECR in the next article.