How to Enable HTTPS Traffic To AWS Application Load Balancer
-
 Chinthaka Dinadasa
Chinthaka Dinadasa - 13 Jul, 2023

HTTPS, or Hypertext Transfer Protocol Secure, encrypts the data transmitted between the client and the server, safeguarding it from potential eavesdropping, tampering, or unauthorized access.
Enabling HTTPS ensures the confidentiality, integrity, and authenticity of the exchanged information, providing users with the trust and confidence they expect when interacting with your application.
By default, ALB listens for HTTP traffic, but when we need to open our API or any application with HTTPS enabled route, we can open it through HTTPS enabled application load balancer.
In this article, we will explore how we should configure HTTPS with an AWS application load balancer with the SSL certificate we requested in the previous article.
Security Group Change For HTTPS
For the moment we have created and attached a security group called javatodev-ecs-app-lb-sg to the application load balancer.
But in that security group, we have only been allowed to access the HTTP (80) port to the public. But since we have to setup SSL enabled route we should open HTTPS (443) to the public.
Open the security group and add the following,
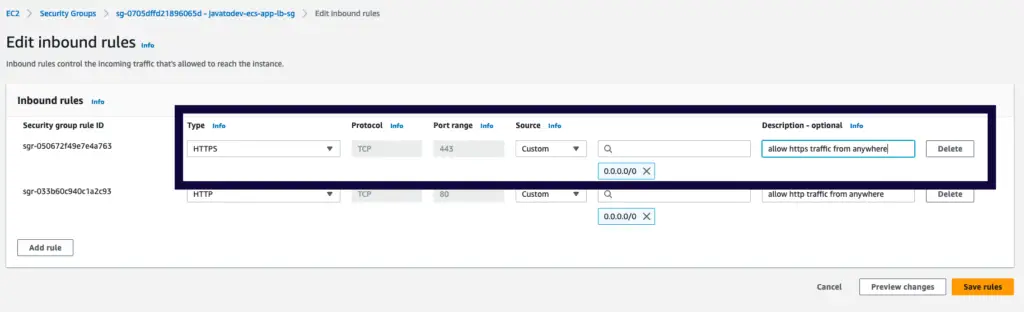
Opening HTTPS with security group configurations
Setting Up HTTPS Listener For Load Balancer
Now we can create one more listener which listens to the HTTPS (443) traffic and routes the same as we route the HTTP (80) traffic inside load balancer listeners.
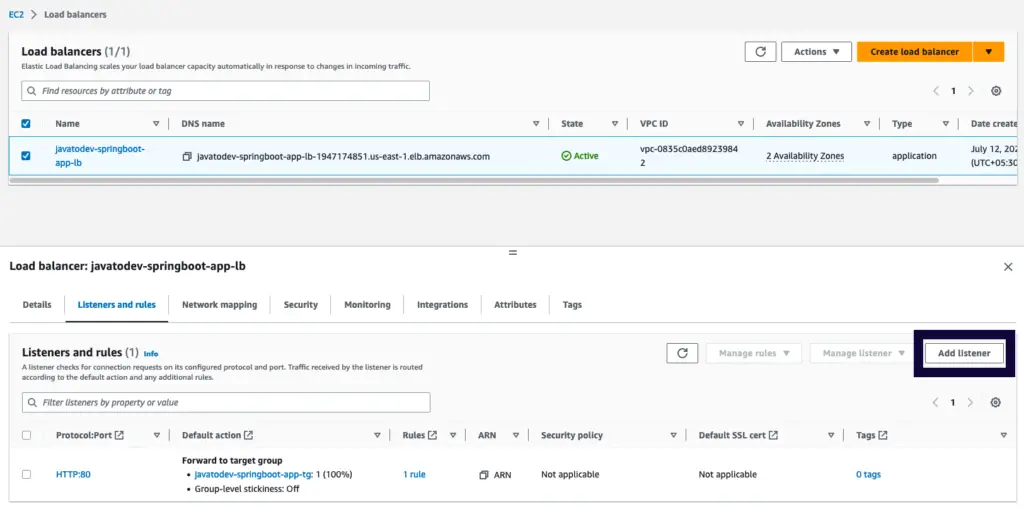
Add a listener for the application load balancer
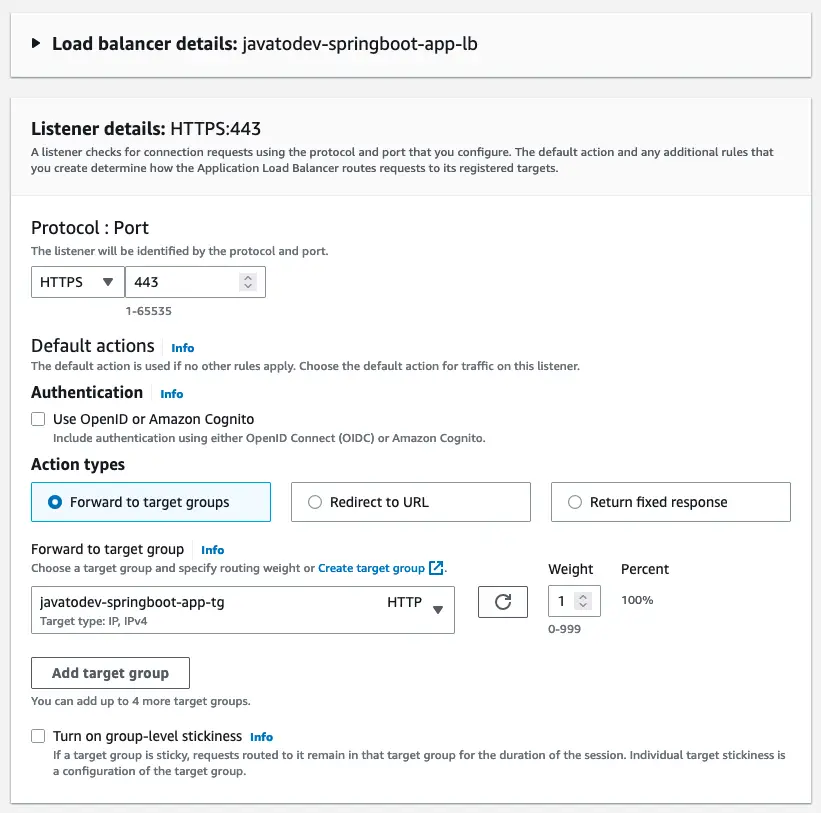
Forward HTTPS traffic to the target group
Then we should point to the correct certificate that we got from the AWS certificate manager.
AWS Certificates are regional resources hence keep in mind when you request SSL certificates and ensure both the certificate and load balancer are in the same region.
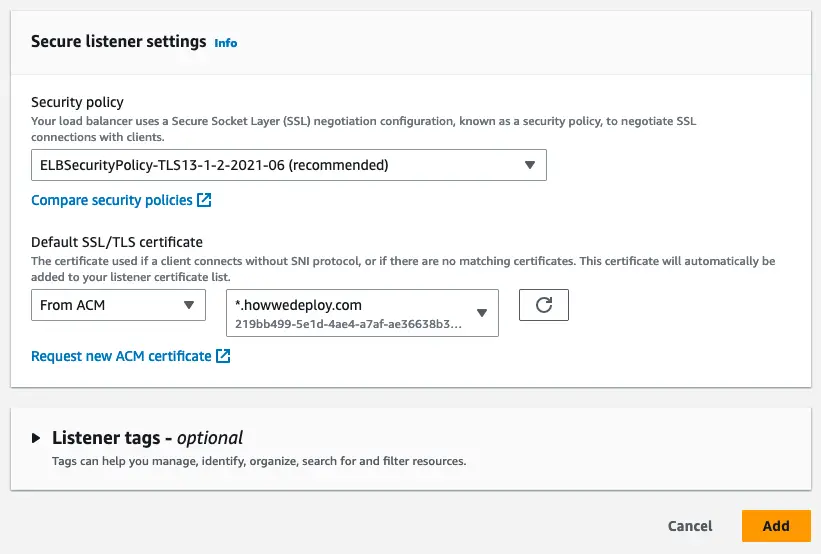
Pointing SSL certificate from ACM to the LB listener
Done, now we have a listener with a valid certificate, and let’s access it with HTTPS URL.
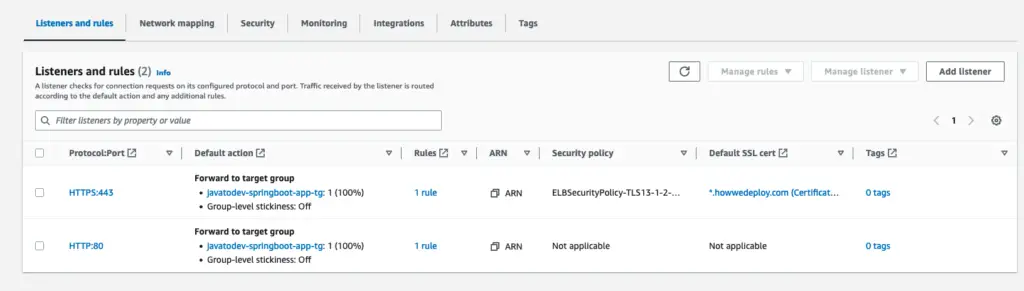
HTTP / HTTPS Listeners which forward traffic to the same target group
Accessing API through HTTPS Enabled URL
Conclusion
Now with this article on enabling HTTPS for AWS application load balancer, we have fully completed our article article series on Deploying Spring Boot Applications With AWS ECS Fargate.