How to Create Security Groups For ECS Deployment
-
 Chinthaka Dinadasa
Chinthaka Dinadasa - 09 Jul, 2023

One essential aspect of securing AWS deployments is the effective use of security groups. Security groups act as virtual firewalls, controlling inbound and outbound traffic to and from AWS resources.
By properly configuring security groups, organizations can fortify their infrastructure, mitigate risks, and enhance their overall security posture.
This article explores the security group requirement and how we should configure all the security groups for ECS fargate deployment that enables secure connectivity between components inside the whole architecture.
Security Group Requirement
With this architecture, we mainly need to have 3 security groups, which are
-
A security group that will manage inbound traffic for the public-facing load balancer that should allow port 80 (HTTP) from the public.
-
A security group that allows 8080 (Spring boot container runs on 8080 port) traffic from API gateway SG, to connect fargate container and public facing API gateway.
-
RDS database security group (Already created on RDS database initialization stage). Here we should allow MySQL traffic from SG that is attached to AWS fargate container.
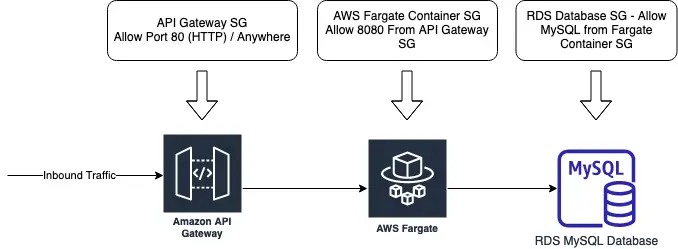
Security Group setup for AWS fargate deployment
Creating Security Groups
We can find security group configurations under the EC2 module in the AWS dashboard. First, navigate there and follow the following steps.
EC2 -> Network & Security -> Security Groups -> Create Security Group
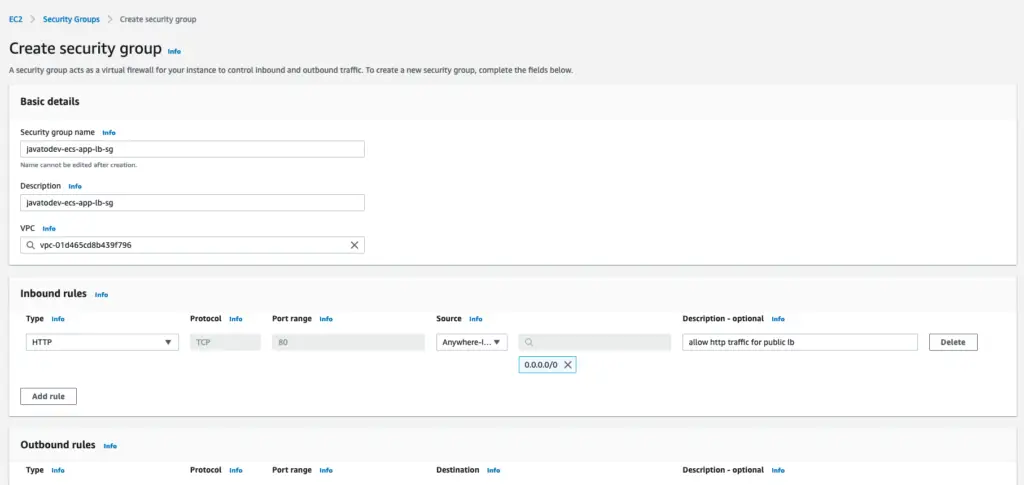
- Security Group for public load balancer - javatodev-ecs-app-lb-sg
-
Inbound rules - HTTP Port 80 from Anywhere 0.0.0.0/0
-
Outbound rules - Keep default (All traffic)
-
Security group for load balancer
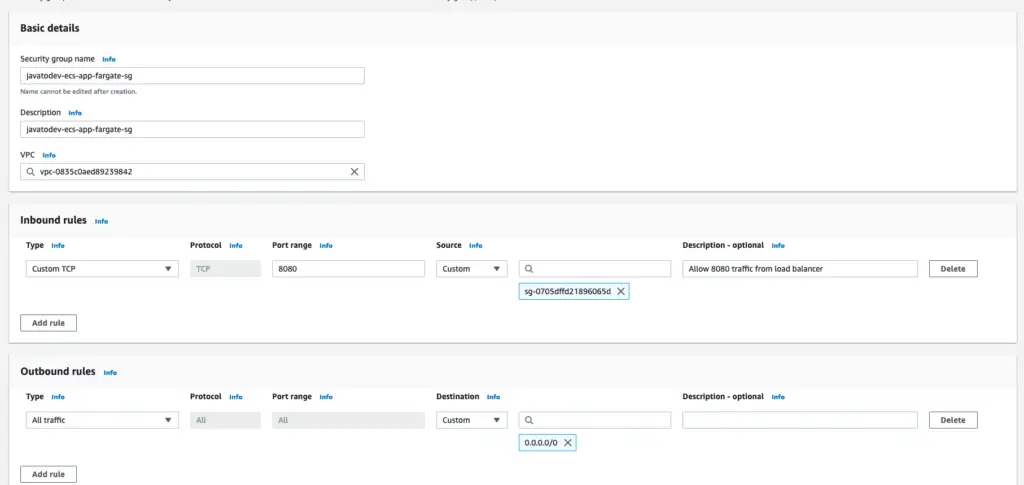
- Security group for API containers - javatodev-ecs-app-fargate-sg
-
Inbound rules - 8080 port from javatodev-ecs-app-lb-sg security group.
-
Outbound rules - Keep default (All traffic)
-
Security group for containers deploy with fargate
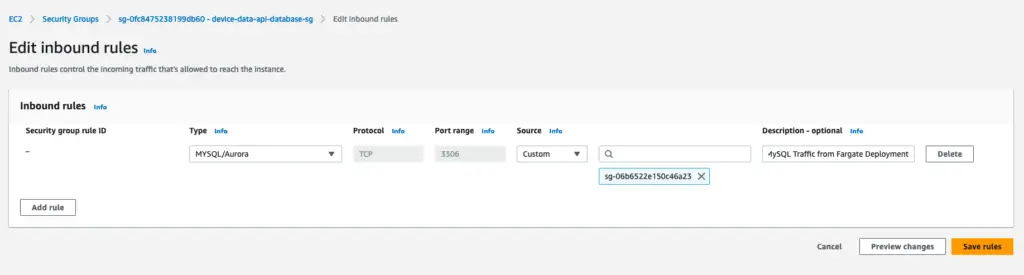
- Security group for RDS database - device-data-api-database-sg
-
Inbound rule - MySQL 3306 from javatodev-ecs-app-fargate-sg security group.
-
Outbound rules - Keep default (All traffic)
-
Security groups for RDS database
Conclusion
We are done with setting up the necessary security groups for our application architecture deployment in ECS fargate in this article series.
Now we can focus on the next step which focuses on creating ECS cluster for our deployment.